Attributing media files using our new open source tool “mift”
For many years Control-F has produced and shared many Python scripts, making them available to delegates attending our training courses. These scripts cover a multitude of functions, such as assisting with repetitive forensic tasks, or helping to report artefacts which might be missed by commercial forensic tools. We are proud to now be going one-step further in announcing our new, free, open-source tool, “mift”.
“mift” is an open-source software tool designed to assist digital forensic examiners in understanding the context of media files on iOS and Android devices. mift can help explain:
- How a media file within the DCIM/100APPLE folder on an iOS device came to be there (taken by the device camera, created via an app, sent vs. received etc.)
- Whether an image file has been shared via the cloud – and if it has, which device it was shared from
- Which primary image a recovered thumbnail image relates to
- Which website a user was visiting when a screenshot was taken
- And more!
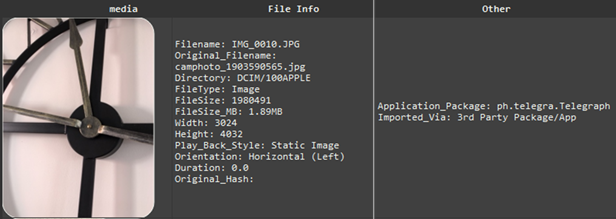
Although the image in the screenshot below is located alongside camera photos in the folder DCIM/100APPLE, the “Application_Package” and “Original_Filename” metadata confirm that the image was created by the camera within the messaging app Telegram.
mift can highlight valuable data which may not be fully decoded and presented by commercial forensic tools. It has already been used by customers to support evidential investigations, and the feedback has been extremely positive. You can get a flavour of its capabilities from an introductory guide available here.
mift is an open-source tool – which means that it is not only free, it’s inner workings are open to scrutiny and review. It’s just one of a series of tools we’re making available via our GitHub repository.
Take a look and get in touch. We’d love to hear your feedback!
