This document is intended to accompany the slide presentation “Has Anyone Seen A Career Path Around Here?” first delivered by Kevin Mansell in June 2014.
About this document
This document is intended to accompany the slide presentation by Kevin Mansell of Control-F, entitled “Has anyone found a career path?” and provides further detail than can be conveyed via the slides alone.
The role of a mobile forensic examiner
The job of a mobile forensic examiner is multi-faceted and complex. Mobile devices often need to be coaxed and coerced into yielding their contents. Once data has been extracted, items of evidential interest are not always immediately obvious and may require skilful analysis in order to locate and interpret them.
Added to these technical aspects of the role, mobile device examiners worldwide are faced with the challenge of examining increasing numbers of ever more complex devices with limited resources. The danger of slipping into treating mobile forensics as a “handle turning” exercise is real and ever present.
The wider organisation in which the mobile forensic examiner is employed is likely to have a very limited understanding of what the role actually entails. Mobile forensics may be seen as some sort of magic, or perhaps more worryingly as a simple low-skilled role: plug in the device, click some buttons, print the report and move on to the next device.
This lack of understanding of what mobile forensics actually involves is damaging in two ways:
Staff churn
Until the role is properly understood by management and human resources departments, job descriptions for mobile examiners will not properly reflect the role being performed. This already means (in the UK at least) that mobile forensic examiners are often paid less than their colleagues employed as computer examiners due to mobile forensics being perceived as being a less skilled job. Consequently highly skilled mobile forensic examiners will transfer to computer forensic roles for more pay, move to another organisation for a wage increase or leave the field entirely. All three of these outcomes are damaging to mobile forensics as a discipline and the criminal justice system that they serve.
Miscarriages of justice
Evidence recovered from mobile devices, and the testimony given by the examiners who recover it, affects people’s liberty. There have been miscarriages of justice in the UK and elsewhere where forensic evidence has either been mishandled, misinterpreted, overstated or ignored. To date there has not been a “headline” case in the UK where mistakes relating to mobile forensic evidence have led to a miscarriage of justice, but if it can happen with DNA and other “traditional forensic” disciplines, it is only a matter of time before mobile forensics, forensic examiners and their employers fall under the spotlight for the wrong reasons.
Mobile forensics isn’t what it was
Just ten years ago, most mobile phones didn’t have cameras, memory cards, Internet access or GPS functionality. Although cheap “burner” handsets without those capabilities can still be purchased, almost all new handsets are smartphone devices1.
Those changes are part of the reason why mobile device forensics is becoming ever more complex: we have more devices which can perform more tasks. At the same time, we have a wider array of techniques for recovering data from mobile devices. The decision as to how to process a particular evidential exhibit coupled with the skilled analysis required to locate and interpret key evidence has never been more important.
Many organisations employing mobile forensic examiners are deploying kiosk-based products operated by staff who do not have a background in digital forensics, typically to process devices associated with volume crime. These staff will not have the same skills or experience as examiners within a dedicated forensic unit. Although this is not a problem in itself, many organisations fail to properly distinguish between the two roles.
Just as paramedics play a vital role in healthcare provision, dealing with a huge range of medical scenarios, there is also a need for “generalists” in the field of mobile forensics. Equally, we expect our healthcare providers to employ skilled anaesthetists, surgeons and consultants; highly trained and experienced staff in specialist roles. In mobile forensics we need to encourage the development of specialist staff with specific skills: bypassing security mechanisms, interpreting mobile web artefacts, de-soldering flash memory chips, recovering deleted data from smartphone app databases etc.
Employers of mobile forensic examiners need to recognise the different dimensions of the job and build organisational structures where staff can progress and be promoted into specialist roles. However, before that can happen we need a model that describes mobile forensic examination in sufficient detail to allow accurate job descriptions to be written. The remainder of this document proposes such a model.
1 A search in June 2014 of the comprehensive database on www.gsmarena.com reveals that of the 46 devices (handsets and tablets) listed as “Coming Soon”, 44 are Android devices, 1 runs Windows Phone 8 and another runs the Tizen Linux-based operating system; in other words all are smartphone devices. In March 2010, only 3 years ago, only 35% of the “Coming Soon” handsets were smartphones
Overview of the Model
This document and the accompanying slide presentation propose a 3-level model, informally described as consisting of levels at 50,000 feet, 5,000 feet and 5 feet. The use of imperial units should not preclude use of this model in countries that state altitudes in metres!
High Level Description (50,000 feet)
At a high level, mobile device forensics can be considered as consisting of acquisition of data from mobile devices and analysis of that extracted data. In many organisations these two roles will be performed by the same person (examiners typically had to be a “jack of all trades”), but it is important to note that this need not be the case. There are today, and increasingly will be in the future, advantages from having staff specialised in either the acquisition or analysis aspects of mobile device forensics.
Acquisition can be broken down into the following sequence of tasks. Although these tasks may often be conducted by the same person for a particular device examination, this need not be the case.
- SELECT an appropriate acquisition tool and extraction type based on the type of device and case requirements
- EXTRACT data from the device in accordance with recognised digital forensics principles, local operating procedures and the law
- EVALUATE extracted data to assess the success of the acquisition and the need for further data extraction (and return to Step 1 if appropriate)
- PRODUCE extracted data in a format which is usable by the recipient
Steps 1-3 in particular are skilled tasks. Step 3 (“Evaluation”) is especially important due to the real possibility that a particular extraction tool/technique will only recover a subset of all relevant data from a particular device and hence further examination will be required.
Analysis can be broken down into the following sequence of tasks. Again, these need not necessarily be conducted by the same person for a particular examination.
- ESTABLISH the requirements for any analysis based on input from the case officer (what does the investigating team hope to achieve by examining the device?)
- ANALYSE the extracted data in accordance with those requirements
- REPORT results from the analysis in a format which is usable by the recipient
- EXPLAIN the significance of reported data in written and verbal testimony
Middle Level Description (5,000 feet)
Mobile device forensics requires knowledge and practical skills in the following five subject areas. Note that the sub-topics listed should not be considered a comprehensive list, but rather as examples of which each subject area involves.
1. Principles
- Digital forensic principles
- Relevant legislation
- Exhibit handling, continuity/“chain of custody”
2. Devices
- How mobile devices behave
- What data mobile devices store
- Types of mobile device
- Connection interfaces
- Mobile operating systems
3. Acquisition
- Extraction techniques (e.g. manual, logical, physical, JTAG, chip-off etc.) and what they can/cannot recover
- Extraction tools – how to operate a specific tool and what functionality it provides
- Troubleshooting acquisition problems – Has an acquisition failed? If so why?
4. Data
- Fundamentals of digital data
- Numbering schemes – e.g. decimal, binary, hexadecimal
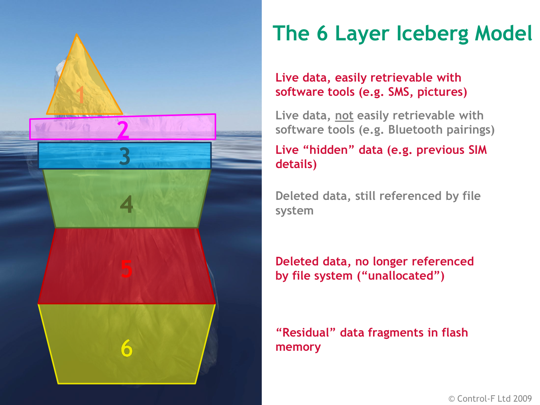
- File systems – live vs. deleted vs. unallocated, characteristics of flash memory etc.
- Working with raw data – e.g. working in a hex viewer, nibbles, bytes,offsets etc.
- Analysis tools – recovery of live and deleted data using tools
- File signatures and file carving
- Searching raw data
- Decoding and interpretation of raw data (e.g. timestamps, encoded or encrypted data)
- Tool development – writing scripts or other software tools to automate data recovery and interpretation
5. Reporting
- Converting recovered data into appropriate formats
- Producing written reports and witness statements
- Giving verbal testimony
Low Level Description (5,000 feet)
Each of the five subject areas defined at the middle level can be broken down further into competencies and expected outcomes. Benjamin Bloom, a prominent American educational psychologist described learning in a particular area as consisting of a spectrum of skills (Bloom, 1956)2. A skills spectrum can be considered similar to a ladder with less demanding skills at the bottom, building in complexity to higher order skills at the top. For example, when considering thinking (“cognitive”) skills, low order tasks often involve simply recalling information. As learning progresses, an individual should able to apply knowledge to a task or problem. Evaluation skills such as comparing, contrasting and judging are at the highest level.
Petty summaries Bloom’s structure for learning as follows (Petty, 2004):
- Full learning only comes from learning skills at all levels
- Higher order skills are dependent on lower order skills being mastered first Using acquisition of data from a mobile device as an example, we can start to identify competencies at different levels:
- EVALUATE: “Compare and contrast four different methods of extracting data from mobile devices and provide an example scenario of where each might be appropriate”
- APPLY: “Which of the following extraction techniques could be used to recover previous SIM details from a Samsung GT-I9100 handset?”
- STATE: “Define the term logical extraction”
These expected competencies can be used to define learning objectives and can form the basis of assessment programmes; in other words we can define what we expect a mobile forensic examiner to be able to do.
In order for the model proposed here to be truly useful, the five subject areas (and sub- topics) defined at the middle level need to be refined, completed and then broken down into competencies at the different levels of Bloom’s Taxonomy. Including experienced mobile forensic practitioners from different organisations and countries in completing the model is critical to ensuring that it is representative and has practical application. Volunteers are welcomed!
2 Bloom’s work has the daunting title “Taxonomy of Educational Objectives”, put simply it is a structure for learning.
Using the Model
Once complete, this model can be used to write job (accurate) descriptions and provide input to workplace performance evaluations, structure training programmes and assess examiner competency. Organisations can use the model to better understand the skillsets of their staff and to ensure that they have staff with capabilities across all of the relevant subject areas.
Importantly, if the wider forensic community can agree on what a mobile forensic examiner could and should be able to do:
- Minimum competency standards for different roles (for example, a “Triage Examiner” or “Smartphone Data Analyst”) can be agreed at an organisational level. If successful, this could be used to define a national competency standard within a particular country.
- Job grading and pay scales can be aligned fairly with computer forensic examiners and the wider organisation. This lays the foundations for improved career progression opportunities within mobile forensics and reducing the costs of staff churn
Conclusions
This document has proposed a three level model to describe the role of a mobile forensic examiner. It is hoped that this can be used to enhance understanding of the role played by mobile examiners within an organisation, reduce staff churn and raise standards in mobile device forensics.
Further work is required to develop the model and feedback on it is welcomed via email to kevin.mansell@controlf.co.uk Updated versions of this document will be made available at www.controlf.net/downloads
Bibliography
Bloom, B. (1956). Taxonomy of Educational Objectives. Handbook 1: Cognitive Domain. Longman. Petty, G. (2004). Teaching Today – A Practical Guide. Nelson Thornes.