Just how much of the web activity on a mobile device are you seeing?
Recovering web activity from a mobile device will be important in many investigations. Which sites has the user visited? Which pages on those sites did they access? What searches did they run?
Although pre-installed browsers like Safari and Chrome are well supported by commercial forensic tools, there is a very real chance that web activity in other apps could easily be missed during a forensic examination. A user might be accessing the web via a wide range of apps, and in some cases not even realising that they are doing so:
- A user may have installed a 3rd party web browser and chosen to use it instead of, or alongside, Safari or Chrome
- Apps like Outlook, Twitter and Instagram default to launching their own “in app browser” when users click on links within the app (e.g. within a direct message, tweet or post)
- Many apps which aren’t web browsers in the traditional sense, access data on the web (and record their activity) – for example a parking app, a cinema app etc.
Our experience indicates that all three of these scenarios may mean that there is web activity on the device which might be extracted, but has not been decoded by commercial forensic tools.
However, we have good news!
Many Android apps utilise the open-source Chromium framework when they access the web – which means that lots of different apps are generating very similar (and decodable) artefacts.
In order to be allowed on the iOS App Store, all apps which browse the web must be based on the WebKit framework – again this means that different apps will produce similar artefacts.
We have released “shomium“, an open-source tool for locating, decoding and reporting web activity on mobile devices. It quickly identifies Chromium-based apps within full file system extractions of Android devices, and likewise alerts the user to Webkit-based apps within extractions of iOS devices.
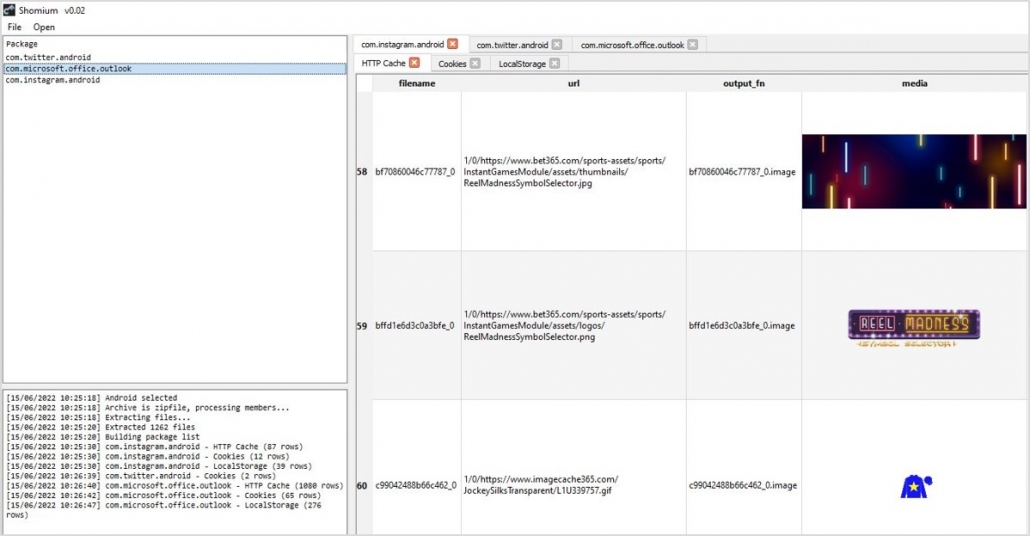
Users can browse contents of the application’s web cache, decoded cookies and “local storage” and then generate HTML reports to pass to case officers and investigation teams.
You can download shomium from our GitHub repository now. We hope that it helps raise awareness of web activity which might otherwise “fly under the radar”. We welcome your feedback!
