Control-F is now looking for an office-based Course Manager to join our small but growing team. We need someone to take responsibility for creating, delivering and maintaining training course content, ensuring that both materials and delivery remain current, engaging and accurate.
The role
The role involves both classroom delivery of existing training courses, alongside design and development of new training course content. The impact and importance to the business couldn’t be greater: you’ll be “on your feet” in the classroom helping our delegates get to grip with digital forensics and when you’re not teaching, you’ll be helping shape new courses and keeping our current courses bang up to date (which is no small undertaking in the fast-moving world of digital devices!)
Our HQ is located at Wyboston Lakes on the Cambridgeshire/Bedfordshire border. This role will involve teaching at HQ as well as at various other locations.
About you
You’ll have previous hands-on experience as a digital forensics practitioner using MSAB XRY and Cellebrite UFED and will have recognised training courses under your belt (you might have a digital forensics degree, but this isn’t essential). You’ll also have excellent written English and be a clear and confident verbal communicator. Not only that, you’ll be comfortable managing multiple ongoing work activities to ensure that deadlines are met.
If you have experience of the following, they would be a huge advantage:
- Oxygen Detective
- FTK Imager and other computer acquisition tools
- SQL and SQLite databases
- Delivering digital forensics training
- Creating and editing professional PowerPoint and Word documents
- Programming experience in Python, C/C++ or Java
- Reverse engineering
As a person, you’ll be comfortable in the classroom spotlight and good at building rapport with others. You’ll be working within a small team of people who pay attention to the detail and have a “can do” customer-focused attitude.
About us
We’re a digital forensics training provider who deliver classroom and online courses, primarily to law enforcement customers. We’re based just 30 minutes drive from Cambridge, the heart of “Silicon Fen”.
What we’re offering
In return, our Course Manager will have a competitive salary, performance-based annual review, defined contribution pension scheme, 22 days a year annual leave (plus 8 Bank Holidays), the ability to work flexitime, a health cash plan and paid time off for volunteering.
Interested?
We are a small business with a big reputation in our field and we’d love to welcome you to join us. You can download the job description, read more about the courses we’re currently offering or contact us for more details and an ‘off the record’ chat about the role.


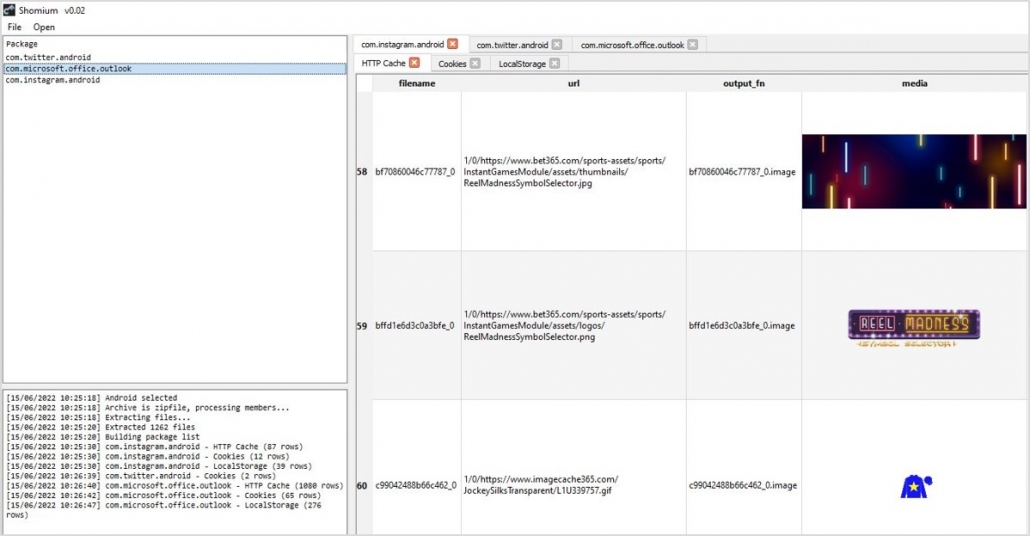
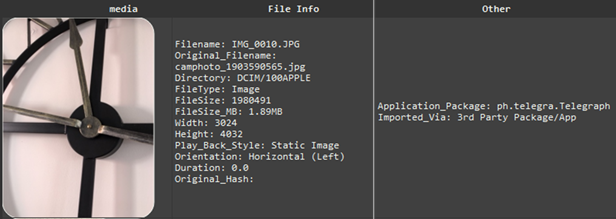

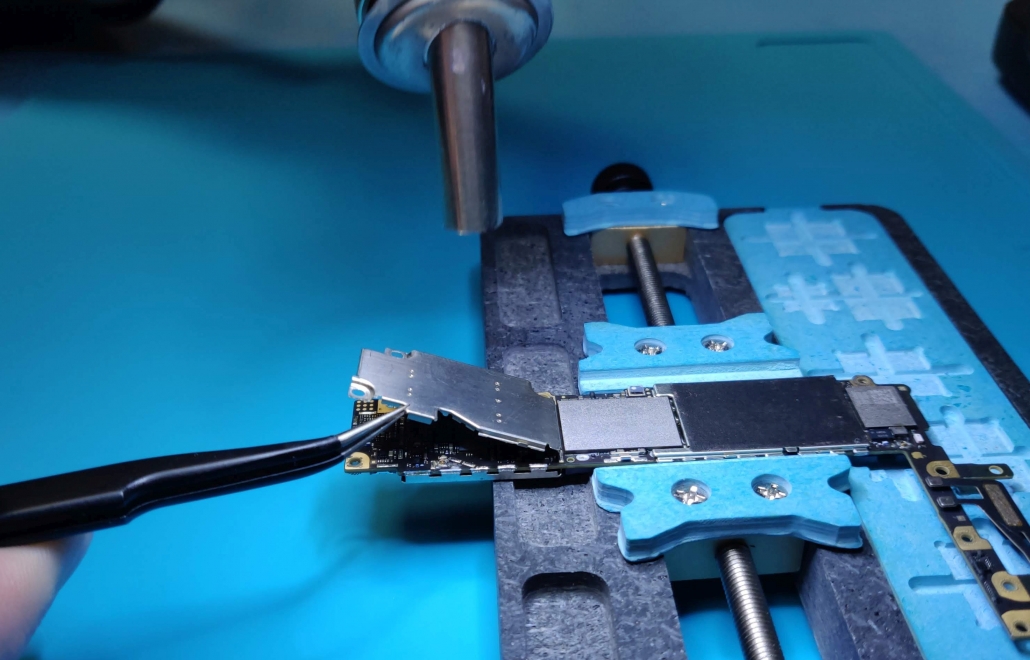
 We’re delighted to announce the release of a new online training programme targeted at operators of mobile forensic kiosks.
We’re delighted to announce the release of a new online training programme targeted at operators of mobile forensic kiosks. 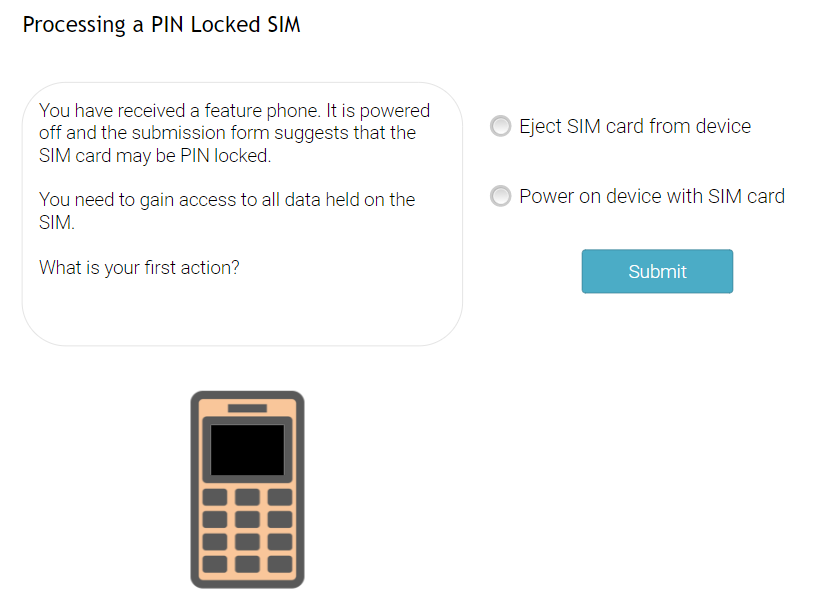
 Control-F Managing Director is taking a day off today after riding 250km (155 miles) in the Dulux London Revolution cycle event at the weekend. Kevin was raising money for
Control-F Managing Director is taking a day off today after riding 250km (155 miles) in the Dulux London Revolution cycle event at the weekend. Kevin was raising money for